[VERDESEC Archival Post 3 of 10]
At VerdeSec, we believe in equipping students with practical tools and knowledge to close the gap between their textbook and working in the industry. To this end, we hosted an online sharing session titled “Hosting Your Own Honeypot at Home Using T-Pot.” This interactive session provided participants with step-by-step guidance on deploying a honeypot using T-Pot: https://github.com/telekom-security/tpotce.

The session began with a hands-on walkthrough of the setup process, covering everything from downloading T-Pot to building and deploying it effectively. Participants learned how T-Pot integrates multiple honeypot technologies into a single, streamlined solution, making it ideal for enthusiasts and professionals alike.
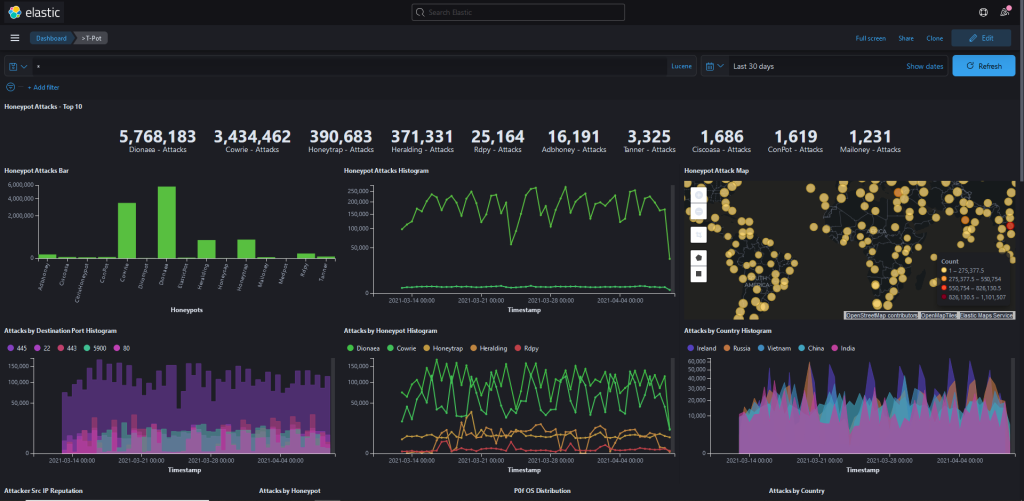
To highlight T-Pot’s capabilities, we showcased the results after running the honeypot for a week. The data revealed a variety of interactions, ranging from automated scans to targeted attack attempts, providing participants with a glimpse into real-world cyber threats. This demonstration emphasized the value of honeypots as a safe and controlled way to study malicious activity.
Another key highlight of the session was the integration of Elastic Dashboard. We demonstrated how to visualize and query the data collected by T-Pot, enabling deeper analysis of trends and patterns in threat behavior. This segment underscored the importance of effective data analysis tools in understanding cybersecurity threats.
The session saw an excellent turnout, thanks to the support of TAR UMT FOCS that broadcasted the event to RIS students. Feedback from participants was positive, with many finding the session quite informative.
By providing practical, hands-on knowledge, this event exemplified VerdeSec’s commitment to empowering the next generation of cybersecurity professionals.
| Activity Details: | |
|---|---|
| Venue: | Online |
| Price: | FREE |
| Participants: | 150 |
| Level: | Beginner |
